Key takeaways:
- Cyberthreats are very common, and one strategy to counter these includes blocking malicious or suspicious IP addresses.
- Blocking IP addresses is possible through multiple methods and operating systems—from Windows to routers.
- Aside from blocking external IP addresses, you can also hide your IP address to enhance your online privacy and security.
As of 2024, there were about 35 billion recorded data breaches, among other types of cyberattacks online. As businesses become increasingly interconnected through the internet, it’s important to implement proactive security measures, including IP blocking.
Thousands of new malicious IP addresses are identified each year, which makes it imperative to stay ahead of potential threats by implementing effective IP-blocking strategies. Many internet servers offer basic website security that can ward off some infiltration attempts, but some crafty criminals slip through the cracks.
So, what can you do? Learn the best ways to protect yourself from external threats.
This guide will teach you how to block an IP address from different operating systems, browsers, and devices.
What is an IP address?
An Internet Protocol (IP) address is a unique numeric identifier assigned to each device connected to a network. It can be compared to a home address but for your phones or laptops connected to the internet. Each device is assigned a unique IP address that allows it to interact with, receive information from, and otherwise contact other devices and networks on the internet.
What are the different types of IP addresses?
Not all IP addresses are the same. In fact, there are multiple types that have their own uses. The main types include:
- Public
- Private
- Static
- Dynamic
Let’s discuss each one:
Public
This is the unique address your internet service provider (ISP) assigns to your network. It’s how your network communicates with the rest of the internet. Public IPs are globally routable and visible to all other devices on the internet. Every public IP address currently active is also unique.
It allows external devices or services such as websites to locate and communicate with your router and internal devices.
For example, when you open Google on your browser, your request will include your public IP address so that Google’s servers know where to send the information.
Private
A Private IP address is a non-routable address assigned to devices within your local network (e.g. home or office). These addresses are not directly accessible from the public internet and are only unique within their specific local network.
This IP address enables connection between devices within the same network. For example, you want to print a document from your laptop to your wireless printer. Both of these devices would use their private IP addresses to locate each other on your network.
Static
As its name suggests, static IP addresses are permanent and unchanging. These are typically configured manually by network administrators. Usually, static IPs are necessary for devices or services that require consistent accessibility at the same address.
For example, if you host a website from your own server, a static IP ensures that internet users can always find your site at the same address.
Dynamic
Unlike static IP addresses, dynamic IPs change regularly. This type of IP address is common for home networks because they’re generally more cost-effective (no financial charge). They are common in user devices like smartphones and laptops.
For instance, if you restart your home router, your ISP might assign it a new public dynamic IP address from their pool, and your laptop might get a new private dynamic IP from your router.
What do IP addresses look like?
Even though most internet users connect to the internet using an IP address daily, the majority don’t know what an IP address looks like.
It can take two forms: IPv4, which stands for Internet Protocol version 4. and IPv6, which stands for Internet Protocol version 6.
IPv4
Invented in the 70s, IPv4 was the first wave of IP addresses. Generally, IPv4 addresses are composed of four numbers between 0-255, separated by dots or periods. It may look like: 99.31.235.187.
Since the early days of the internet, IP addresses were assigned using the IPv4 model. But we’ve used up all available IPv4 addresses, which has led us to adopt IPv6. While most devices still use IPv4 to connect to the internet, the shift toward IPv6 began in earnest in 2011 when it was officially launched.
IPv6
On June 6, 2012, organizations like the Internet Society and major internet service providers launched IPv6 to accommodate the growing number of devices online. They made sure the number of conceivable IPv6 addresses is enormous and won’t run out anytime soon.
It uses a hexadecimal digit system, separates groups using colons, and may include letters like 2001:0db8:85a3:0000:0000:8a2e:0370:7334.
Why do you need to block IP addresses?
A business, educational institution, or internet user would attempt to block specific IP addresses for several reasons. In general, the most common reasons are:
- Blocking bots, spammers, and hackers. Bots, spammers, and hackers attempting to infiltrate your website can strain your bandwidth and reduce access speed for users. It’s also detrimental to sales if you run a business online.
- Limiting website access. Many academic institutions and businesses use IP blocking to restrict the websites that students or employees visit. The goal is typically to increase productivity by limiting distractions.
- Protecting data. Hackers often attempt to infiltrate websites to steal data or other vital information. That information can be used to blackmail or otherwise undermine a company.
- Maintaining confidentiality. Many academic institutions and companies that keep sensitive records—like transcripts, health records, etc.—are regularly targeted by hackers. Identifying malicious IP addresses and placing them on a blocklist keeps those records safe and confidential.
- Controlling traffic. Blocking IPs helps manage traffic to a website or network by restricting access from specific locations or known problematic IPs, which can improve website performance and reduce server load.
- Enhancing privacy. Blocking IPs can be a method to prevent stalking, harassment, or other privacy intrusions, mainly if these issues are traced back to specific IP addresses.
- Complying with legalities. Some businesses may need to block IPs from certain countries or regions due to trade restrictions, copyright laws, or other regulatory compliance requirements.
How to block an IP address
Here’s how to block an IP address using Mac, Windows, Linux, routers, web hosting, and Google Analytics.
Blocking an IP address for Mac users
To block an IP address on your Mac computer, you’ll need access to your wireless router (or LAN router, which connects to the internet using an Ethernet cable), as macOS does not provide a straightforward GUI-based method for IP blocking directly on the system. It’s important to know the router password, which can often be found printed or stuck on the outside of the modem.
- Go to the Apple menu. Find the Apple logo in the top left corner of your computer screen.
- Select system preferences. Open the dropdown menu and select System Settings. Once the menu appears, find the icon labeled Network. Press the Details bar at the bottom of the screen. Navigate to the TCP/IP tab, where you should find your IPv4 or IPv6 address. Take note: this will only provide your local IP and not the external address you want to block.
- Log in your router. Next, log into your router. Again, password information is typically outside the router, but you can always contact your network administrator if you’re having trouble.
- Restrict access. Once you’ve logged into your router, a list of enabled and disabled IP addresses should appear. From there, most routers will give you the option to deny access to unique IP addresses or an entire range of addresses. Some routers also have the option to block a website. After blocking the IP address, your network will be protected from that address.
Blocking an IP address for Windows users
Blocking IP addresses on a Windows computer requires going through the Windows Firewall. In tech terms, a firewall is a component that allows your computer to block access to your network without inhibiting your ability to communicate with outside networks.
- Locate website to block. Open your internet browser and locate the website you want to block. Highlight and copy everything that comes after the “www” in the web address.
- Open Command Prompt. Navigate to your Start menu and open Command Prompt (Admin).
Type ping website.com and press Enter. Replace “website.com” with the domain name of the website. The command will display the IP address of the website. Command Prompt should respond by generating several lines of code, which should reveal the website’s IP address.
Alternatively, you can type nslookup website.com. Highlight and copy the IPv4 or IPv6 address.
Return to your internet browser, paste it into the search bar, and press Enter. Confirm that it takes you back to the website.
3. Open Windows Firewall. Open the start menu. Locate Control Panel. From there, find Windows Defender Firewall and open it.
4. Advanced settings + Windows Inbound Rules. With Windows Firewall open, locate and click on Advanced settings on the left side of the screen.
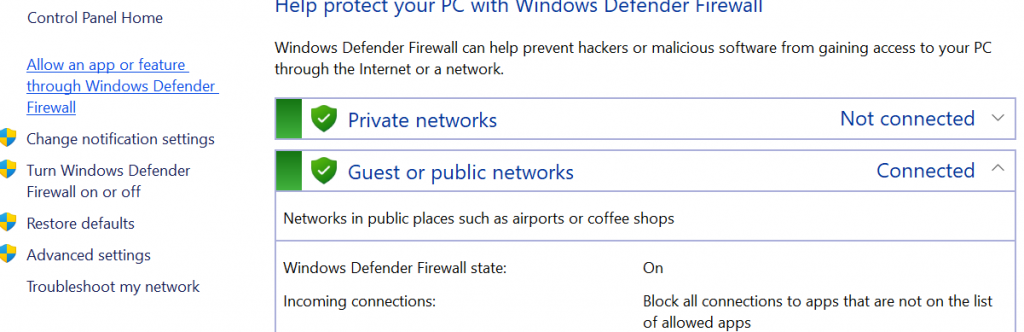
Then, locate Inbound Rules near the top left of the screen. This should change the menu options. On the right portion of the window, find and click New Rule.
5. New Rule. With the New Rule tab open, select the Custom option and press Next.
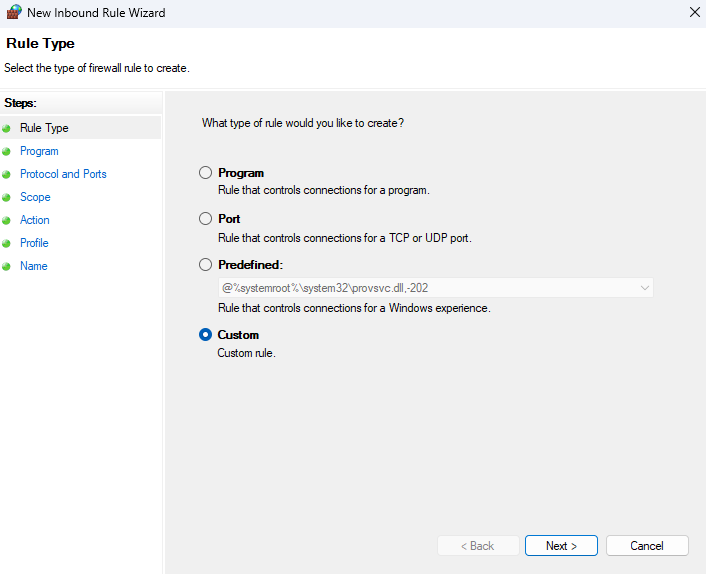
Choose All programs to apply the rule to all programs or specify a program path if you want to block the IP for a specific program. Then, click Next.
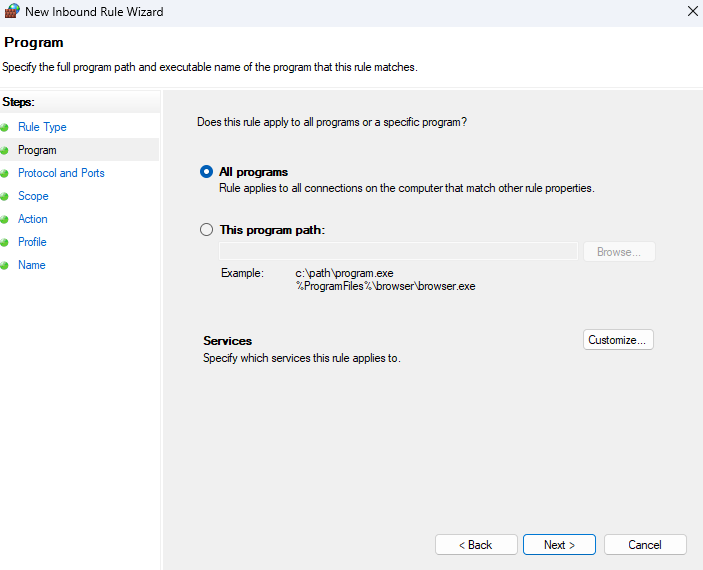
6. Protocol and Ports. Leave the default settings (Any) or specify if needed, then click Next.
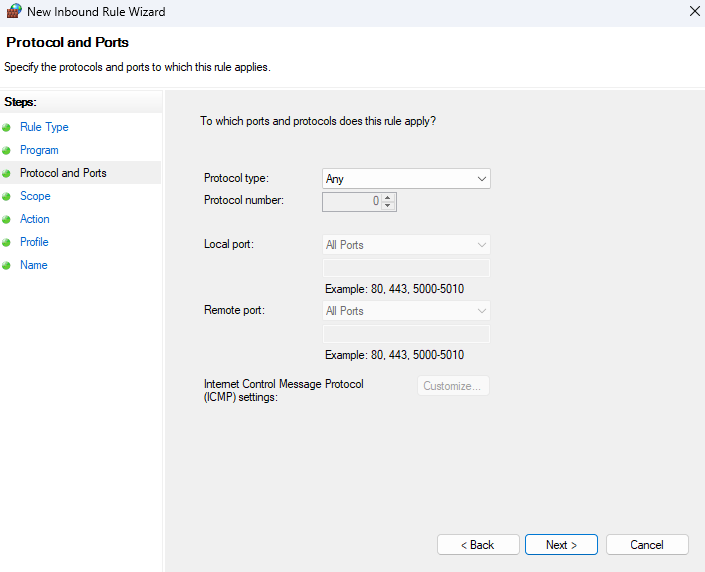
7. Scope. Under Which remote IP addresses does this rule apply to?, select These IP addresses. Click on Add to specify the IP address you want to block. You can enter a single IP address, a range, or a subnet. Click OK, and then Next.
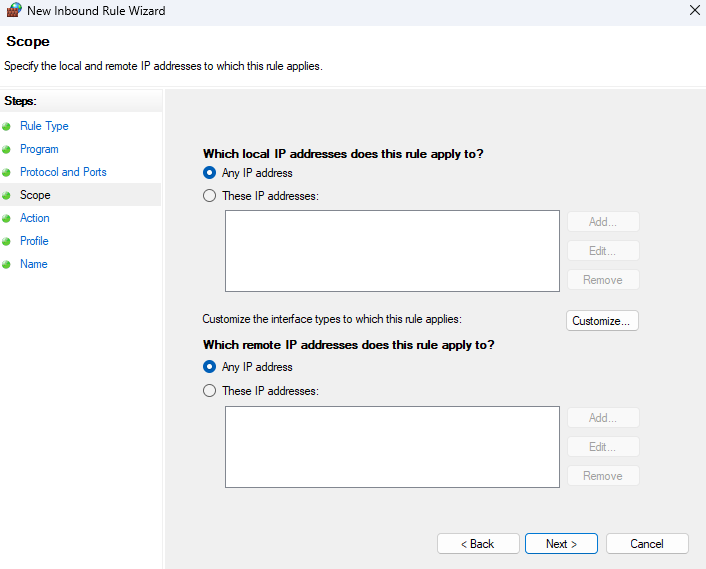
8. Action. Choose Block the connection and click Next.
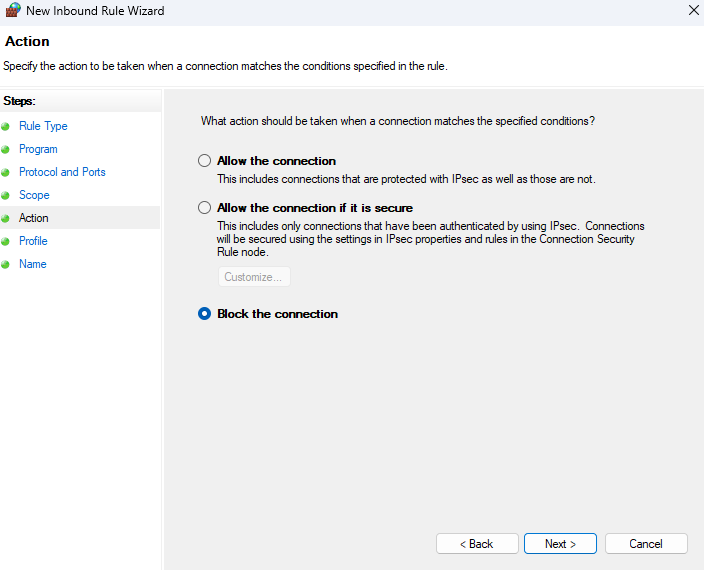
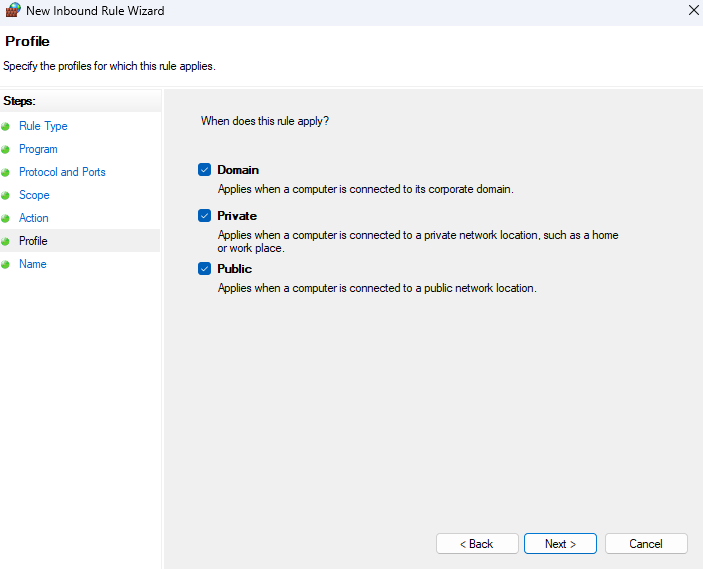
9. Profile. Select when this rule applies (Domain, Private, Public). It’s safe to select all if you are unsure, then click Next.
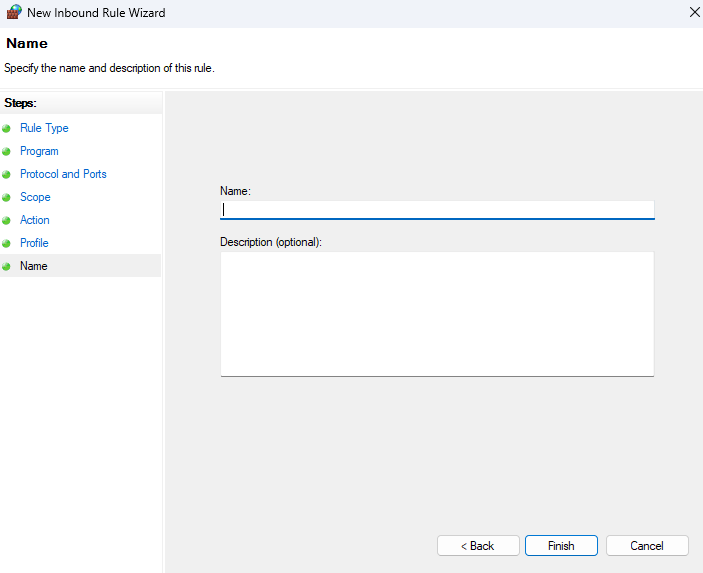
10. Name. Give the rule a name and an optional description, then click Finish.
Blocking IP addresses for Linux users
Linux needs a different process for managing network security and blocking IP addresses. Here’s how you can do it using iptables:
- Open the Terminal. You can find the Terminal application in your system’s utilities or search for it in your application menu.
- Block with iptables. Once the Terminal is open, use iptables, a powerful tool Linux users use to manage network traffic. To block a specific IP address, enter a command like this:
sudo iptables -A INPUT -s [IP address] -j DROP
In this command, replace [IP address] with the IP address you want to block. Here’s what each part of the command does:
- Sudo. Runs the command with administrative privileges, ensuring you have the right to modify firewall settings.
- iptables. The command to modify the firewall rules.
- -A INPUT. Appends a rule to the input chain, which handles incoming traffic.
- -s [IP address]. Specifies the source IP address that you want to block.
- -j DROP. Tells the system to drop packets from the specified source, effectively blocking the IP address from accessing your system.
Blocking IP addresses for routers
When you block IPs on your router, you secure all devices on your network by controlling all internet traffic in one place. This is simpler than using command-line tools on systems like Linux and affects more devices. It’s a practical way to improve network security and manage bandwidth.
Here’s a step-by-step guide to do it through your router’s interface:
1. Access the router interface. Log into your router through its web interface, which you can access by typing the router’s IP address into the web browser’s address bar.
Shared IP addresses for routers are 192.168.1.1 or 192.168.0.1 and varies depending on your router manufacturer. You’ll need your username and password, which are often set to default values like ‘admin’ and ‘password’ unless you have changed them.
2. Locate IP blocking options. Once logged in, navigate to the router’s security settings. This section might be labeled differently depending on the router’s firmware; look for terms like Firewall, Security, or Access Control. Here, you will find options to manage IP blocking. Enter the certain IP addresses you want to block. Depending on your router’s capabilities, you may be able to block individual IPs or ranges of IPs.
3. Entering IP addresses. There should be a field where you can type in the address you want to block. If you want to block multiple IP addresses, you need to add each separately or specify an IP range.
4. Applying and saving changes. After entering the IPs, be sure to apply or save the changes. Otherwise, your settings may reset once you log out or restart the router.
Blocking IP addresses for web hosting services
When you block IP addresses on your web hosting service, it protects your entire website no matter where it gets accessed. It’s a simple and effective way to keep your online services safe and manage who can visit your site from anywhere in the world. It’s more efficient than blocking IPs on your computer or local network, which only protects the devices connected to that network.
Here’s how to manage IP restrictions through your web hosting control panel:
- Access the hosting control panel. Log into your web hosting control panel. It’s typically accessible through your web hosting provider’s website, where you must enter your username and password. Once logged in, you’ll be directed to your control panel’s dashboard or home page.
- Locate IP blocking tools. Search for the IP blocking feature within your control panel. This may be under sections like Security, Firewall Settings, or IP Deny Manager. The exact naming can vary depending on your control panel, such as cPanel, Plesk, or others.
- Navigating to IP blocking. Once you find the IP blocking section, click on it to open the settings to manage IP restrictions.
- Enter IP addresses to block. In the IP blocking interface, there should be an option to add new IP addresses to the block list. You can typically enter a single IP address or a range of IP addresses to block.
- Single IP Blocking. If you want to block a specific IP, enter it in the provided field.
- Range Blocking. To block a range of IPs, you might need to use CIDR notation (like 192.168.1.0/24) or input a start and end IP address, depending on the options provided by your hosting service.
- Apply and save changes. After entering the IP addresses or ranges you wish to block, save, or apply the changes. There might be a button or link to click that will update the settings. Confirming these changes is important to ensure that the IPs are indeed blocked.
- Verify the settings. After blocking the IPs, it’s a good idea to verify that the settings are working as intended. You can check this by accessing your site from the blocked IP addresses (if you have access to them) or by monitoring access logs for any further activity from those IPs.
Blocking IP addresses in Google Analytics
Blocking specific IP addresses in Google Analytic ensures the accuracy of your website data by preventing activities that can skew key metrics like page views, bounce rate, and conversion rates.
To block IP addresses in Google Analytics, you need to use filters. Here are steps you should follow:
- Go to Admin > View > Filters.
- Then go to Add Filter and name your filter
- Filter Type > Predefined > Exclude > Traffic from the IP addresses.
- Choose That are equal to.
- Fill out the details of the IP address you want to block.
- Click on Save.
Note: Those using Google Analytics 4 will need to follow a different set of steps. You can check out Google’s Analytics Help for more details.
Troubleshooting common IP blocking issues
You might encounter a few common issues when implementing IP blocks to secure your network or website. Troubleshooting these problems ensures that your security measures don’t block legitimate users or fail to block malicious traffic. Below, we explore some of these typical issues and offer detailed steps to resolve them.
Blocked IPs are not taking effect
Sometimes, even after you set rules to block specific IPs, these blocks are not taking effect. This can leave your network vulnerable, so promptly address these issues.
- Verify firewall rules. Double-check your firewall settings. Make sure that all configurations are correctly implemented and active. This includes ensuring that the rules are applied to the right network domain and have the correct priority in your firewall’s rule list.
- Check IP entries. Verify that the IP addresses are in the correct format and match those intended for blocking. Pay attention to potential typographical errors or misplaced segments in the IP address.
- Restart equipment. Sometimes, changes may only take effect once the network equipment is restarted. This can apply to both routers and firewalls. A simple reboot can often activate the new settings, making your IP blocks effective.
Legitimate access blocked
On occasion, IP blocking can unintentionally affect legitimate users and restrict their access to your network or website, which leads to frustration and disruptions in business operations.
- Review the blocklist for errors. Regularly inspect your blocklist for any incorrect entries. This includes checking for IPs that should not have been listed or legitimate IP ranges mistakenly blocked due to an overlap with broader blocked segments.
- Adjust rules. You may need to adjust your firewall rules if legitimate IPs are blocked. This involves whitelisting certain IP addresses or modifying the criteria to block IPs to be more specific and prevent overblocking.
- Check for false positives. Ensure that your security settings are calibrated correctly. Overly aggressive security measures can sometimes block legitimate users, so finding a balance that maintains security without being overly restrictive is essential.
Difficulty finding IP address
Identifying the correct IP addresses to block is fundamental to effective network management. If you’re having trouble pinpointing which IPs to block, here are some methods to help:
- Use online tools. There are numerous tools available online that can resolve domain names to their corresponding IP addresses. These tools can be invaluable when you know the domain but not the IP.
- Check website logs. Your website’s access logs provide insights into the traffic it receives. Reviewing these logs allows you to identify potentially malicious activity based on IP addresses and take appropriate action.
Best practices for blocking IP addresses
When safeguarding your network through IP blocking, it’s vital to follow a set of best practices to ensure that your efforts are practical and balanced. Proper IP blocklist management and security settings help protect against threats while ensuring legitimate users can access your network without disruptions. Here’s how you can maintain an optimal balance:
- Update blocklists. Regularly update your blocklists to reflect the evolving threat landscape. Add new suspicious IPs as threats are identified and remove IPs that no longer pose a risk.
- Review security settings. Continually reassess your security protocols to ensure they remain effective against current threats. This includes verifying that your firewall and other security tools are configured correctly and functioning as expected.
- Maintain user access. Carefully manage your IP blocking strategies to ensure you don’t accidentally block legitimate users. Regular reviews and adjustments can help prevent such issues.
- Use automated tools. Leverage automated systems for managing IP addresses to reduce the likelihood of human error and streamline updating and applying blocklists.
- Implement a broader security strategy. View IP blocking as one element of a comprehensive security strategy. This integrates various defensive measures to create a multi-layered defense system.
- Enhance with additional measures. Augment IP blocking with additional security measures, such as intrusion detection systems and regular security audits, to ensure a thorough and robust protection scheme.
How to block or hide your own IP address
Many people prefer hiding their IP addresses for various reasons. Most of the time, it’s because of privacy and security reasons. For instance, some users hide their IP addresses because cybercriminals can use these details to track your location.
Meanwhile, hiding your IP address could also grant access to geographically restricted websites.
The good news is, there are many ways you can block or hide your own IP address. Here are two practical ways:
- Use a VPN
- Use a proxy server
Use a VPN
Virtual private network (VPN) helps conceal your real IP address by replacing it with another. It routes your internet connection through a private server that effectively masks your online identity.
How to use a VPN
Using a VPN typically involves selecting a service, installing its application, and connecting to a server. The exact steps vary slightly by device, but the general steps for most devices include:
- Choose a VPN provider. Research and select a reputable VPN service. Consider factors like privacy policy (e.g., a no-logs policy), server locations, speed, and pricing.
- Download the app. Depending on your device, download the VPN from:
- Directly on the provider’s official website (computers of all operating systems)
- Official app store (Google Play Store for Android or Apple App Store for iOs)
- Install the app. Run the downloaded installer (for computers) or simply open the app after downloading (for mobile/streaming devices). Follow any on-screen prompts.
- Sign up or subscribe. Create an account and choose a subscription plan that fits your needs. There are applications that offer free plans but come with limited features and data caps. Also, try free trials for paid subscription plans first to see if the service covers everything you need.
- Connect to a server. Most VPN apps offer a quick connection option that automatically selects the fastest available server, which is usually geographically close to you. But you also have the option to manually select a server from a different country or region if you want to access geo-restricted content.
Use a proxy server
Aside from VPNs, proxy servers are also another method to hide your real IP address and access online content. A proxy server acts as an intermediary between your device and the internet.
How to use a proxy server
Using a proxy server involves configuring your device’s network settings or using specific browser extensions. Unlike VPNs that often have dedicated apps, proxy setup is typically done manually or through browser add-ons. Here are steps to follow:
For Windows devices:
- Go to Settings > Network & Internet > Proxy.
- Under Manual proxy setup, toggle Use a proxy server to On. Also, toggle the Automatically detect settings to On.
- Windows will prompt you to follow your proxy server’s instructions once you have one available.
- Go to Automatic Proxy Setup once Windows finds a proxy auto-config file, then switch the Use Setup Script to On.
- Input the scrip address and click Save.
For Mac devices:
- Go to System Preferences > Network.
- Select your active network connection (e.g., Wi-Fi or Ethernet) and click Advanced.
- Go to the Proxies tab.
- Select Auto Proxy Discovery > Secure Web Proxy.
- Enter the proxy server address and port number.
- Click OK.
For Android devices:
- Go to Settings > Network & Internet > Wi-Fi.
- Long-press on your connected Wi-Fi network, then tap Modify network
- Tap Advanced options
- Under Proxy, select Manual
- Enter the Proxy hostname (IP address) and Proxy port.
- Tap Save.
For iOs devices:
- Go to Settings > Wi-Fi.
- Tap the i icon next to your connected Wi-Fi network.
- Scroll down to HTTP Proxy and tap Configure Proxy.
- Select Manual.
- Enter the Server (IP address) and Port.
- If required, enter Authentication credentials you used to sign up with the proxy server provider.
- Tap Save.
Why is my IP address blocked?
A blocked IP address might suddenly no longer access certain websites or services. This could prevent you from using email, streaming content, or even logging into platforms you usually use without problems.
If your IP was blocked by mistake—something that can happen with shared or dynamic IP addresses—you’ll need to figure out what caused this and talk to your service provider to fix the issue. Here are several potential reasons for the block:
- Viruses in your device
- Software extensions
- History of illegal activity
- Inappropriate website content
Let’s discuss each in detail:
Viruses and malware in your device
One of the most common reasons that IP addresses are blocked from accessing remote servers is that the remote server detects a virus within your IP address. Internet users often don’t even know they have picked up a virus.
Once you’ve removed the virus or malware from your network, reach out to the website you attempted to access and explain why you should be removed from the blacklist.
Software extensions
There are many ways to customize your internet browser. One example includes extensions that eliminate pop-up ads from websites or detect viruses hiding within a website.
There’s nothing illegal about adding extensions to your browser, but some websites will ban users who run ad-blockers. They may see this as a disruption of their revenue flow.
History of illegal activity
If you have a history of conducting illegal activity online, many website admins will block your IP address as a preventative measure because they think you’re untrustworthy. Online illegal activities may include illicit trade, activity on the dark web, or cybercrimes.
Inappropriate website content
If you operate a website that contains potentially offensive content like pornographic material or illegal trade, you will likely be blacklisted from many websites because your content is subjectively inappropriate.
While you may disagree with the decision of another admin to blacklist your website, the only way around the blacklist is a direct appeal to the admin.
Protect your online presence from cyberthreats
Understanding how to block an IP address is important for maintaining a secure and trouble-free online experience. IP addresses are fundamental in connecting devices to the internet and locating them among countless others.
When a device or website causes issues, identifying its IP address lets you take direct action. You can effectively prevent further unwanted interactions by blocking the troublesome IP address through a straightforward process. This enhances your online security while controlling your internet environment.
Don’t let unwanted online disruptions compromise your safety. Take control today by learning how to identify and block problematic IP addresses. Empower yourself to create a safer and more secure online experience with the right steps and security tools like SiteLock.
Frequently asked questions
No, you cannot directly or easily tell if someone is tracking your IP address in real-time. There is no simple tool for direct detection by an average user.
No, it’s not illegal to hide your IP address nor a website to block IP addresses in the United States.
Yes, you can block an IP address from accessing your network or website.
You can block traffic from a specific IP address by configuring your device’s firewall settings, setting up rules on your network router, web hosting platform, or Google Analytics
You cannot directly block IP addresses on your phone unlike with computers since Android and iOs devices don’t have built-in features (like a firewall) that allow you to block IP addresses at a system level. It’s recommended to configure your router settings instead.
Although, if you want to hide your own IP address, using VPNs and proxy servers can help you achieve a similar result.
Yes, you can block IP addresses based on geo-location. This is a practice known as geo-blocking. Websites and network administrators use specialized services or firewall rules that cross-reference an IP address with a geolocation database to determine its origin country or region.
An IP address can reveal your location down to the city or region. It also identifies your ISP. If you’re not careful, you may be prone to spam, DDoS attacks, impersonations, or direct hacking attempts.
No. It’s a common misconception. Private browsing does not hide your IP address. These browser features primarily prevent your browser from saving your search history, cookies, and site data locally on your device. Your IP address remains visible to websites and your ISP.
Go to What Is My IP Address. It will automatically detect your network and provide its information if it’s not truly hidden. Activate your VPN or proxy server and reopen the website to see if it still displays the same details.
Websites often need to know your IP address for legitimate purposes. These include:
1. Geo-targeting content or advertisements (showing you relevant information based on your location)
2. Gathering analytics to understand user demographics
3. Implementing security measures (like detecting suspicious login attempts or preventing fraud)
4. Defending against cyberattacks (DDos attacks)
In some cases, sketchy free IP blocking tools often sell your data, expose you to malware, or lack proper security and performance. While a few offer legitimate and safe limited free versions, significant dangers like data logging and poor encryption are also common.
Be sure to check reviews and research the company behind the tool. Also check if the platform logs your online activity or needs excessive permissions (for apps).




