Key takeaways:
- A data breach response plan gives small businesses a path to follow when a data breach occurs, so you’re not making it up as you go.
- Quick action and honest communication help you limit the damage and maintain your customers’ trust.
- Looking back at what happened turns those hard lessons into a better plan for next time.
When a data breach hits, everything stops. You’re probably wondering what went wrong, how many people got hit, and what you need to do right now. A data breach response plan provides a practical roadmap for navigating those challenging moments. It tells you who needs to step up, what your response team tackles first, how to secure your systems, and how to reach out to affected individuals and partners without creating further panic.
Here’s the thing about breaches for small business owners: it’s not just computers acting weird. It’s your name on the line. It’s customers losing trust. It’s running your business while putting out fires. Having a plan before trouble shows up keeps you from spiraling. A simple communication plan means you’re not making it up as you go. Most people wait until it’s too late to realize they needed one.
Disclaimer: This article is for information purposes only and shall not be taken as legal advice. Please consult a data breach specialist for your specific use case.
How does a data breach impact a business?
A security incident can wreck your day in minutes. You may need to shut down systems while your team attempts to isolate the affected systems and determine what has been exposed. Orders get backed up. Support tickets start piling up. Everything you normally do gets put on hold because you’re stuck dealing with the breach.
Then there’s the legal side of things. A data breach response team might need help from legal counsel to handle legal and regulatory requirements, manage breach notification, and work with agencies like the United States Department of Health and Human Services (HHS) if you’re dealing with regulated data. When sensitive data is compromised, your customers start inquiring about identity theft protection or credit monitoring.
Here’s a real example of why being prepared matters. A small retailer discovered that someone had gained access and stolen passwords. The business had to shut down the affected systems, reach out to customers, and activate its incident response plan. But here’s the problem: they didn’t have a plan ready. So decisions took forever, and the shutdown dragged on way longer than it should have. A quicker response could have reduced the risk and prevented the damage from spreading.
Learn the basics of cybersecurity to protect your business before a breach happens.
What is a data breach response plan?
A data breach response plan is your go-to document that maps out what happens after a security incident. It breaks down how to respond when a breach occurs, who needs to step up, and how to protect people and systems while you handle legal and regulatory requirements. For small businesses, it turns a stressful moment into a set of steps you can actually follow instead of guessing your way through it.
Here’s what a data breach response plan does for you:
- Gets you moving fast when a breach pops up so you can limit further risk
- Gives roles to your response team and other key team members
- Protects sensitive data and cuts down exposure across affected systems
- Keeps you on track with legal obligations like breach notification rules
- Helps you talk to affected individuals, partners, and other stakeholders who need to know
- Walks you through recovery so you can reduce financial loss and reputational damage
The plan won’t stop breaches from happening. But it helps small businesses respond with purpose and system when one hits.
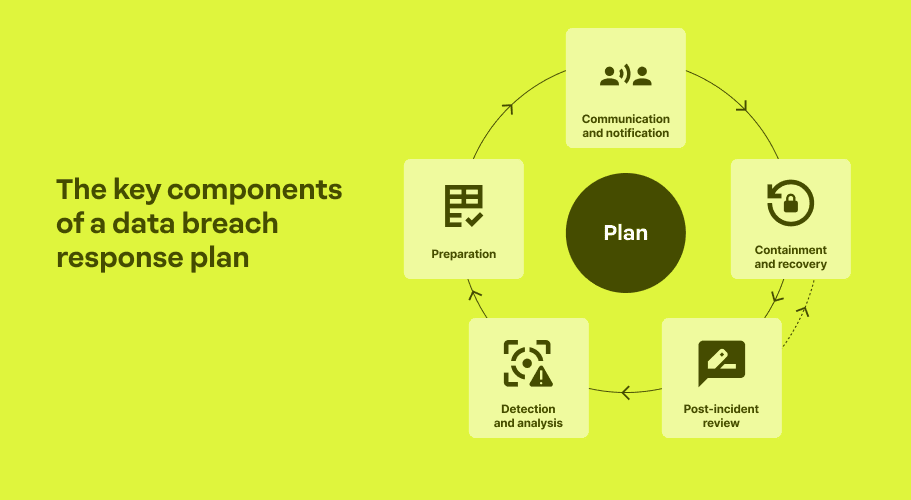
Key components of a data breach response plan
A data breach response plan gives small businesses a simple structure to follow during a security breach. Here’s your overview of the main parts and how they work together.
Core pieces of most incident response plans include:
- Preparation
- Detection and analysis
- Containment and recovery
- Communication and notification
- Post-incident review
Preparation
This is the work you do before anything goes wrong.
- Figure out who’s involved in incident response: your IT people, human resources, and legal counsel.
- Know where your important data sits through basic data mapping.
- Get basic security measures and threat detection tools up and running.
- Set expectations for data protection and access controls.
Detection and analysis
This is how you confirm something’s actually wrong.
- Use detection systems to catch unusual activity or a suspected breach.
- Determine if the issue is a genuine breach or merely a false alarm.
- Consider the systems and data that might be involved.
- Save details you might need later for data forensics.
Containment and recovery
This phase is about stopping the damage and getting back to work.
- Lock down the incident and limit unauthorized disclosure.
- Protect affected systems and accounts.
- Restore access only after you’ve done security checks.
- Apply fixes so the same thing doesn’t happen again.
Communication and notification
This part covers who needs to know and when.
- Follow your communication plan to avoid scrambling.
- Reach out to affected individuals as needed.
- Loop in business partners if their systems or data got hit, too.
- Stay up-to-date with reporting rules, such as the HIPAA breach notification rule (if applicable).
- Offer help like credit monitoring when identity theft is a concern.
Post-incident review
This is where you turn the lessons learned into something useful.
- Examine what worked and what held you back.
- Update your response plan based on what really happened.
- Tighten up your security for next time.
How to create a data breach response plan (step-by-step)
A data breach response plan may sound technical, but it’s really just a set of practical steps. Each one is simple on purpose. The goal is to help you act with direction when a security incident happens, not to turn you into a cybersecurity expert.
Here’s how to put it together:
- Prepare your plan and people
- Set up detection and initial analysis
- Contain the security incident
- Recover and restore normal operations
- Notify and support affected parties
- Review and improve the plan
Step 1: Prepare your plan and people
Anticipate a breach before it even happens.
- Assign owners for your incident response plan, including IT, legal counsel, and operations.
- Determine who will lead when a security breach is confirmed.
- List your most important systems and customer data as part of a basic risk assessment.
- Write down how to protect data and limit adverse consequences.
This step turns scattered knowledge into a comprehensive plan your team can actually follow. So, make sure your key team members understand their roles from day one.

Step 2: Set up detection and initial analysis
You need a way to catch trouble early.
- Use simple tools or alerts to flag a suspected breach.
- Define what triggers an initial analysis.
- Decide who confirms whether a real incident has happened.
- Record what systems and accounts might be involved.
Catching things early helps you limit damage to affected systems and customer data. It also gives you more time to handle breach notification requirements properly.
So, strengthen your defenses with DNS security solutions that block threats before they reach your network.
Step 3: Contain the security incident
Once a breach is confirmed, act fast.
- Secure accounts and limit access to affected systems
- Pause risky activity while the issue gets reviewed.
- Protect customer data and internal records as part of data protection.
- Focus on stopping the spread, not fixing everything at once.
This step is about control and short-term security response. The faster you contain it, the less damage it will spread to other parts of your business.

Step 4: Recover and restore normal operations
After the threat is under control, shift to recovery.
- Fix the issue that caused the breach.
- Restore systems and return to normal operations.
- Check that access controls and backups work as expected.
- Confirm data is safe before reopening systems.
Recovery helps your business move forward with less disruption. Getting back to work quickly shows customers you’ve got things handled.

Step 5: Notify and support affected parties
Some breaches require outreach.
- Notify affected individuals when required by law.
- Work with legal counsel on timing and message.
- Address concerns related to identity theft when personal data is involved.
- Keep communication direct and factual.
This step helps protect trust and meet legal duties. But keep in mind that timing is crucial here. Please note that state laws vary, and notification deadlines may differ.

Step 6: Review and improve the plan
A plan should never sit untouched.
- Document what worked and what slowed response.
- Update steps based on real experience.
- Regularly review and test the plan as systems change.
- Adjust roles and contacts as the business grows.
Ongoing review keeps the plan useful and relevant. Looking at the root cause of each incident response helps you spot patterns and fix weak spots before the next issue hits.

Frequently asked questions
The purpose of a data breach response plan is to give your business a simple incident response plan to follow when a security issue happens, so you can act fast instead of guessing. It helps you do a quick risk assessment, apply the right security measures, and reduce problems like identity theft while protecting your customers and your business.
A company’s data breach response plan should cover preparation, detection, containment, recovery, and post-incident activity so teams know exactly what to do at each stage. These steps help restrict access, meet regulatory compliance and federal laws, mitigate risks, and protect the company’s reputation after a breach.
After proactive preparation, the first step in an actual data breach response is detection and analysis. From there, you execute containment, which means securing systems right away to stop further exposure of financial information and other data. This includes a quick risk assessment, steps to detect anomalies, and actions like network segmentation to limit how far the issue can spread.
It may be worth suing if your confidential information was compromised and resulted in actual harm, such as fraud, identity theft, or ongoing financial loss. If there is no clear damage, many people affected focus instead on monitoring accounts, watching for potential threats, and reporting the issue to the company or local police if needed.
The company that owns or controls the information compromised is typically legally liable for a data breach, even if a vendor is responsible for it. This is especially true when breach notification rules under state laws aren’t followed. Liability often comes down to the root cause, how staff handled the response, and whether delays or poor communication led to further damage, including harm to customers or public trust.
Brave through a data breach with a strong plan
When a data breach occurs, the businesses that recover faster aren’t the ones with the most tools. They’re the ones with a plan they can actually follow. A solid data breach response plan gives you direction when things get messy. It helps your team act with purpose, manage breach notification, and communicate with external stakeholders without adding confusion or delay.
No plan is perfect on day one. What matters is having something in place and continually improving it over time. Every incident brings lessons learned, whether it’s about systems, people, or how such information should be handled in the future. Regular updates turn those lessons into stronger habits and fewer mistakes.
If you want to lower your risk before the next issue pops up, strengthening your website security is a smart place to start. We offer website security services designed to help small businesses protect their website, reduce exposure, and support the response steps outlined in your plan. Getting prepared today makes the next incident easier to handle tomorrow.
See how our website security tools can help protect your business and support your breach response plan.